Computer Security Day: Why MailStore Admins Need to Know About SSL Warnings and Certificates
In 1988, November 30 was designated International Computer Security Day. Launched by the US Association for Computer Security, Computer Security Day aims to raise awareness of the importance of backing up data, keeping software updated, checking passwords and privileges, and so on and so forth – the list is endless. In the 30 years since Computer Security Day came into being, IT security has become much more complex; thus, it can be a major challenge for IT administrators to guarantee the security of a whole company’s IT systems and stay up to date with the latest technology. For this reason, the onus is also on software manufacturers to take responsibility and make their solutions as secure as possible. As manufacturers of email archiving solutions, we at MailStore also see it as our duty to help IT admins make computer security more manageable – especially since email archiving software is responsible for protecting a company’s entire email correspondence for years on end. This is why our guiding principle is “security by default”. In a blog article published some time ago, Daniel Weuthen, Director of Engineering at MailStore, explained what was behind MailStore’s Customer Security Awareness Initiative and the measures taken to provide installations with the highest level of protection from the outset.

We’d like to use Computer Security Day to take a closer look at a specific option and security warning in our software, namely the option “Ignore SSL Warnings” or “Accept All Certificates”.
The History of the “Ignore SSL Warnings” Function
The option of ignoring SSL warnings for outbound connections has been available since Version 1 of MailStore Server, so since 2007. However, as this option appeared only when setting up and configuring outbound connections from MailStore Server, it was largely concealed from the administrator during day-to-day use of the software. In subsequent years, as software companies began to appreciate the importance of IT security, browser manufacturers such as Google and Mozilla decided to phase out support for unsecure HTTP and issue prominent alerts whenever an outbound connection was deemed unsecure. We too set ourselves the task of making our solutions as secure as possible by following the recommendations of the security experts; and we’ve always endeavored to keep our solutions simple to use by e.g. delivering software with secure default settings. This also led to a series of adjustments to the option whereby SSL warnings can be ignored.
Ever since Version 10 of MailStore Server and the MailStore Service Provider Edition (SPE), the encrypted IMAP-TLS has been the default protocol used for IMAP profiles, whereas HTTPS has always been the default access protocol for Exchange profiles. At this time, the option of ignoring SSL warnings appeared only when setting up and configuring outbound connections.
Then, in Version 12, administrators would receive an alert on the MailStore dashboard and in the archiving and export results if potentially unsecure outbound connections to email servers or directory services were being used. A connection was deemed potentially unsecure, for example, if it was unencrypted or the “Ignore SSL Warnings” box had been checked when setting up an outgoing connection. The alert level “Information” (depicted by an “i” inside a blue circle) was first introduced to raise awareness of the problem of login data for MailStore products being sent to third-party systems while inadequately protected.
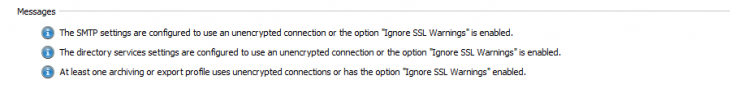
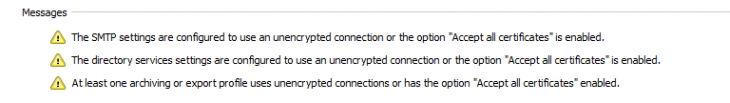
In Version 13, we changed the alert level for unsecure outbound connections from “Information” to “Warning”. Now, administrators would receive a warning on the dashboard and in the results of executed profiles if the outbound connection settings were potentially unsecure. This was done with the aim of encouraging administrators to pay more attention to protecting data communications and to assume responsibility for the safety of user data. Incidentally, as of Version 13, inbound connections to all MailStore products must be encrypted.
Version 13.0.3 that was released only recently features another small but important tweak. Customer feedback relating to the “Ignore SSL Warnings” option – now displayed much more prominently on the dashboard – showed us that the wording of the alert was open to misinterpretation. For that reason, the option now appears as “Accept All Certificates” in the latest version. However, as “accepting all certificates” is an unsecure setting, the software behaves exactly as before.
What Does the Warning Mean – and What Not?
With the new warnings and increased visibility of the option, it became clear that there was some uncertainty as to precisely which SSL warnings were to be ignored. The impression could arise that enabling the option would suppress warnings issued by the MailStore solutions. So, some administrators were astonished to see SSL warnings still appearing on their MailStore dashboards.
Checking the box for this option actually denotes that the SSL warnings generated by the operating system will be ignored and thus specifies that: “As an admin, I want my MailStore product at this point to accept all certificates on my email system” – whether trusted or not. So, if “Ignore SSL Warnings” (“Accept All Certificates” in the latest version) is not enabled, a MailStore product will refuse to execute e.g. an archiving profile if it detects a non-trusted certificate. But if the admin decides to enable the option for unsecure connections, MailStore solutions will ignore the operating system’s SSL warning, execute the profiles, but also issue corresponding warning messages. It is not possible to suppress these alerts. It’s also important to know that MailStore admins will always receive warnings if the option is enabled – i.e. even if they are using a trusted certificate. When using trusted certificates, therefore, it makes sense not to enable the “Accept All Certificates” option in the first place. This option should be enabled only in cases where a temporary scenario – for which no certificates exist or for which certificates are not necessary – needs to be overcome.
The customer feedback we received showed us that we succeeded in drawing attention to this unsecure option. In addition, it allowed us to improve our software on this point.
Unsecure Outbound Connections Are Still Possible, But Unsecure Inbound Connections Aren’t – Why Is That?
As we have full control over our software and, therefore, over all inbound connections, we are able to prohibit all unsecure inbound connections without exception and thus provide maximum security. In the case of outbound connections to third-party systems, however, we are not in a position to recognize all infrastructures and anticipate all potential scenarios. For instance, it is conceivable that a secure certificate simply doesn’t exist for a legacy system that needs to be archived during migration, or that an administrator who has set up a test system attaches no importance to encryption in what is purely a test environment. Although security is our priority, we still want to facilitate email archiving in scenarios like these, even when the connections are unsecure. So, although email archiving can still be carried out, in this case admins will receive a warning to the effect that the current connection settings are not secure and should be changed as quickly as possible.
So, to Conclude:
You should regard Computer Security Day as an opportunity to take a critical look at the security of your IT systems. This includes checking the encryption settings for all your systems’ inbound and outbound connections. Where possible, only trusted certificates should be used. MailStore Server has made it easier for you to use valid certificates since introducing support for Let’s Encrypt™ certificates in Version 12. In order to protect your archive and the critical information contained in your business emails (e.g. requests for quotations, orders, complaints, documents, etc.), we also recommend always using the latest version of MailStore Server, as only by doing so will you benefit from the latest security features, security patches, and bug fixes. So, our recommendation is to keep your MailStore Update & Support Service permanently active, as this is a requirement for installing the latest version of the MailStore software.
More Information
If you’d like to learn more about security, we recommend the following blog articles on our products and product strategy:
Product-related articles on the subject of security:
- Feature Spotlight: Automated TLS Encryption with Certificates from Let’s Encrypt
- Admins enjoy more Secure Mobile Access to Email Archives using TLS Encryption
- How do you Archive Encrypted Emails?
More articles on the subject of security:
- The MailStore Customer Security Awareness Initiative: Why Security Is Our Top Priority
- Security by Default – On the Safe Side
- MailStore Is Keeping an Eye on Security: Enhanced IT Security for SMEs
- The Email is the Modern Business Letter: Security for Archived Emails
- Keep Your Software Up-to-date







