The Gmail Scandal That Really Isn’t a Scandal
 An issue that sounds like the next big data scandal has been doing the rounds in the media over the last few days. Headlines such as ’Google reportedly allows apps to scan some people’s Gmail inboxes’ and ‘Google Has Been Letting App Developers Gain Access To Users’ Gmails, Unsurprisingly’ suggest that Google doesn’t really take protecting Gmail mailboxes all that seriously. But is that really true? And what’s the situation like with other service providers, such as Yahoo! and Microsoft?
An issue that sounds like the next big data scandal has been doing the rounds in the media over the last few days. Headlines such as ’Google reportedly allows apps to scan some people’s Gmail inboxes’ and ‘Google Has Been Letting App Developers Gain Access To Users’ Gmails, Unsurprisingly’ suggest that Google doesn’t really take protecting Gmail mailboxes all that seriously. But is that really true? And what’s the situation like with other service providers, such as Yahoo! and Microsoft?
Where exactly did this rumor begin?
On 2 July, The Wall Street Journal wrote the following in its article ‘Tech’s ‘Dirty Secret’: The App Developers Sifting Through Your Gmail:’
“[…] But the internet giant continues to let hundreds of outside software developers scan the inboxes of millions of Gmail users who signed up for email-based services offering shopping price comparisons, automated travel-itinerary planners or other tools. Google does little to police those developers, ….”
Upon closer inspection of Earny, the online tool mentioned in the article, for example, it becomes clear that it doesn’t just support Yahoo! and Microsoft mailboxes alongside Google accounts, but that you can also grant access to mailboxes from any other provider via the ‘Other Provider’ link. In contrast to Google, Yahoo!, and Microsoft, which support the modern OAuth login method, Earny requests access credentials to access the respective mailbox.
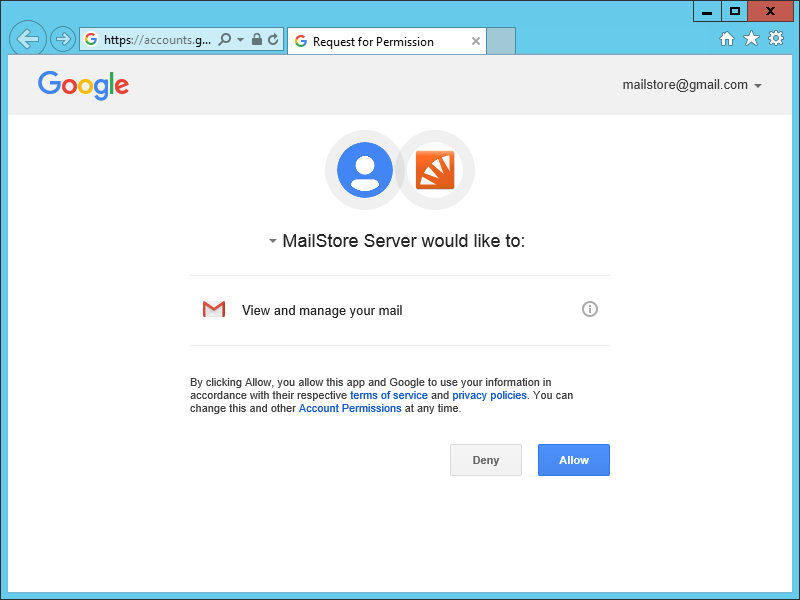
Maximum control, thanks to OAuth
The major difference between forwarding access credentials and authorizing applications or online services via OAuth is the option to individually control the precise scope of access for each application or online service, and revoke this again if necessary.
If a user authorizes an application to access their Google, Yahoo!, or Microsoft account for the first time, for example, they will be shown who has requested access in a so-called consent dialog. An email will often be sent afterwards to inform the account holder about this activity.
Things weren’t better ‘before’
All too often, entire user accounts were taken over, and data was misused to send spam or viruses, for instance, or access sensitive data such as credit card information, all because of weak or stolen passwords.
This is why Google, Yahoo!, and Microsoft have been doing a lot over the last few years to prevent this kind of misuse and make account access more secure. These measures include introducing multi-factor authentication, authorizing applications or online services using OAuth, and blocking ‘insecure applications.’ The latter term refers to applications that have to obtain the username and password to access the respective account. However, this means that you inevitably end up granting unlimited access to the entire account, including your contacts, calendar, or other data that might not even be needed for the application’s actual purpose.
Incidentally, the secure OAuth log-in method is supported by MailStore Server and MailStore Home since version 9.7 when archiving Gmail mailboxes, which means that our products are considered as secure application from Google’s perspective.
A question of trust
While user data and OAuth access credentials remain on your personal computer for standard applications such as MailStore Server and MailStore Home, this is usually not the case for online services. The access credentials, and user data, if required, are stored and processed on the service provider’s servers. Developers coming into contact with data to consistently improve the services on offer is all but unavoidable for online services that primarily revolve around understanding email contents properly and executing automated actions.
Ultimately, this prompts the question as to whether companies such as Google, Yahoo!, and Microsoft are responsible for what third-party applications or online services do with their users’ data. To use OAuth, the respective developer has to first register their application with Google, Yahoo!, or Microsoft, and as part of the process defines the required permission for his particular application or service. This is the only way for the user to obtain the control described above, and therefore guarantees them the maximum level of transparency.
In the end, however, it is always the user who is responsible for putting their trust in an application or an online service and granting it access to their mailbox – with or without the options that OAuth offers.
As a rule of thumb, users of online services and applications should always ask themselves the following questions:
- What is the business model behind this service or application?
- How trustworthy is the company offering the service or application?
- Which access rights does the service or the app need, and does this make sense within the context of the app?
MailStore employees don’t access archived emails
We at MailStore also receive queries now and then from users asking if we have access to our customers’ archived emails. We can say with good conscience that we don’t, as our products are installed and operated by our customers in their own environments.
Daniel Weuthen is Director of Engineering at MailStore Software GmbH.





