![]() The audit log is used to log auditable events inside MailStore Cloud. This includes but is not limited to changing users, groups or retention policies. The log is secured through a blockchain and can therefore be validated. To see and validate the audit log, the user must have the ‘Auditor’ role.
The audit log is used to log auditable events inside MailStore Cloud. This includes but is not limited to changing users, groups or retention policies. The log is secured through a blockchain and can therefore be validated. To see and validate the audit log, the user must have the ‘Auditor’ role.
General rules for auditing are:
- Success is audited if there was something changed (“write”). Successful read operations are normally not audited.
- Failure is audited when it’s due to authentication or authorization, for both read and write operations.
Audit Log
The list view on this page will display activities in either ascending or descending order of the date and time in which they were logged. It also displays the activity type, the actor, and message describing the activity.
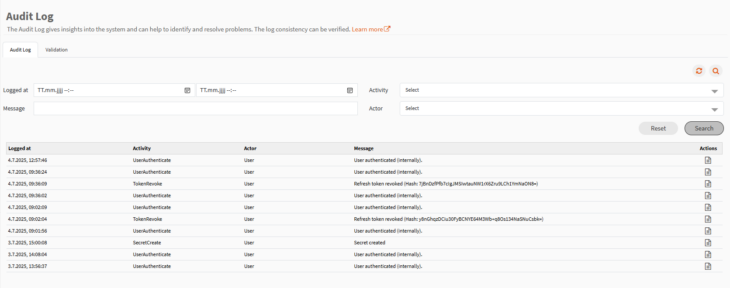
- Search – By clicking the search icon (magnifying glass), a search mask can be opened.
- Search results can be filtered by timeframe, activity and actor. Also, a search term for the message can be defined.
- Refresh – The refresh icon can be used if needed to refresh the page.
- Actions – Allows you to view log entry details.
![]() A maximum of 10.000 search results can be retrieved. If you reach this limit, you have to use the search mask to reduce the number of search results.
A maximum of 10.000 search results can be retrieved. If you reach this limit, you have to use the search mask to reduce the number of search results.
Details
You can view the details of each entry by clicking the corresponding button in the “Actions” column.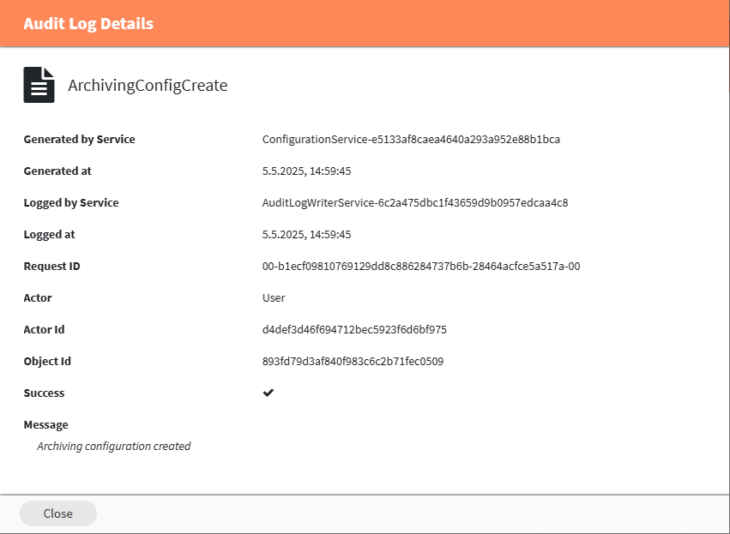
- Generated by Service – Which sub component of MailStore Cloud generated the entry.
- Generated at – Timestamp when the entry was originally generated.
- Logged by Service – Which audit log service did commit the entry to storage.
- Logged at – Timestamp when the entry was committed to storage.
- Request ID – ID of the request that is associated with this entry, e.g. which user request.
- Actor – Type of actor, e.g. a user or a service.
- Actor ID – ID of the actor, e.g. the ID of the acting user.
- Object ID – Object on which was acted upon, e.g. a piece of configuration.
- Success – Whether the action was successful.
- Message – Additional information, providing context and for example a reason for the action.
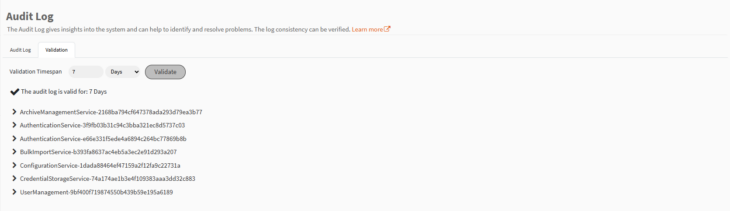
Validation
On the validation page, the validity of the audit log can be confirmed. Entries for the selected time frame will be checked.
Each sub component of MailStore Cloud creates its own hash chain of audit log entries to ensure the integrity. For each sub component, you can view the first and last verifiable entry.